Implement Both Hardware and Software Firewalls: Hardware Firewalls – These are typically deployed at the network perimeter, they are often integrated into routers or dedicated firewall appliances. Software Firewalls – These are installed on individual devices, such as computers and servers, to provide an additional layer of protection.
Configure Firewalls Effectively: Block Unauthorized Access – Set up firewall rules to explicitly deny but allow only necessary and trusted traffic. Restrict Unnecessary Services and Ports – Disable or block services and ports that are not required for normal network operations.
Regularly Update Firewall Rules: Continuously monitor your network traffic and adjust firewall rules as needed to adapt to changing security requirements.
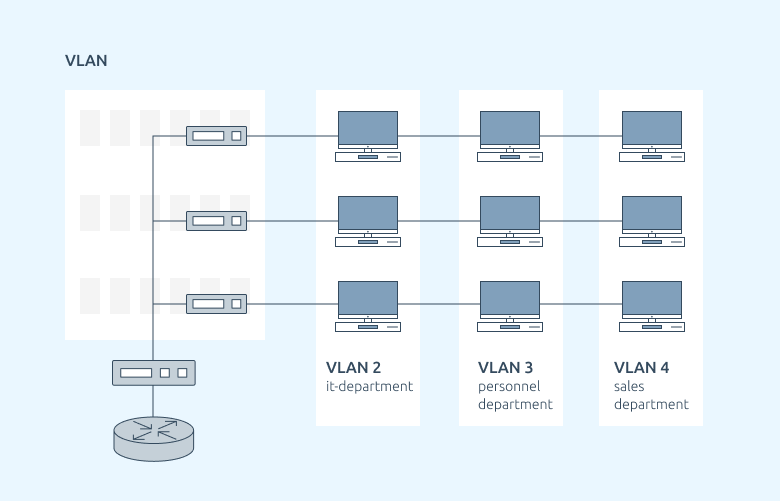
Network segmentation:
Network segmentation is a crucial security practice that involves dividing a network into isolated segments or zones, grouping similar resources based on function and security requirements. This strategy aims to protect critical systems and sensitive data by limiting unauthorized access and lateral movement within the network. It can be achieved through techniques like Virtual LANs (VLANs) or physical separation and is complemented by access control rules, role-based access control, and security monitoring. Regular auditing and maintenance ensure that network segmentation remains aligned with evolving security needs, enhancing overall network security by reducing the potential impact of security breaches.
Strong Authentication and Access Control:
Enforcing strong, unique passwords for network devices and user accounts, along with implementing multi-factor authentication (MFA) for an additional layer of security, is essential in safeguarding against unauthorized access. Access control lists (ACLs) further enhance security by restricting access to network resources based on user roles and responsibilities. These measures not only protect against data breaches but also ensure that users and devices have the appropriate level of access, following the principle of least privilege. Regularly auditing and fine-tuning these controls aligns security practices with evolving requirements, making them indispensable for robust network protection.

Regular Updates and Patch Management:
To maintain a secure network environment, it’s crucial to keep all network devices, operating systems, software, and firmware up to date with the latest security patches. Regularly published security patches address known vulnerabilities and weaknesses that attackers may exploit. Establishing a patch management process is essential to ensure updates are applied promptly. This process typically includes tasks such as patch identification, testing, deployment scheduling, and monitoring. Patch management reduces the risk of known vulnerabilities being exploited by cybercriminals, enhancing overall network security and protecting against potential threats.
Security Monitoring and Incident Response:
Security monitoring is a critical aspect of network protection, involving the deployment of intrusion detection systems (IDS) and intrusion prevention systems (IPS) to continuously scrutinize network traffic for suspicious activities. Real-time logging and monitoring are essential to promptly detect potential security incidents, with regular log reviews aiding in the early identification of threats. Additionally, a well-developed and regularly tested incident response plan ensures a coordinated and efficient response in the event of a breach or cyberattack, minimizing potential damage and downtime while maintaining network security.

Log a ticket and one of our
Tech Titans will give you a shout…